Today, is my first day using a course on Try Hack Me. After creating a free account, I jumped into the Pre-Security learning pathway.
I am learning from the first lab titled Offensive Security Intro, which is an Easy lab, with a recommended time of completion of 25 minutes.
The lab utilizes a command-line application called “Gobuster” which utilizes a brute-force technique aiming to locate directories and pages that could be hidden within. More information on “Gobuster” can be found here.
The command utilized for this lab to brute-force my way into hidden pages was:
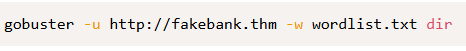
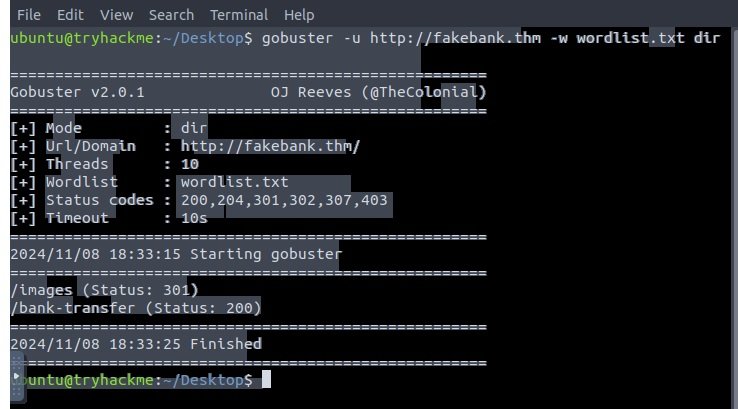
The -u in this context, is utilized to specify the website’s URL.
URL stands for Uniform Resource Locator. In common terms, an URL is the address of a resource on the internet. In this case, the URL or address is: http://fakebank.thm .
The -w in this context, is utilized to tell the tool, to take a list of words found within the “wordlist.txt” file, and search the URL with those words to find any potential hidden pages.
In this case, http://fakebank.thm/bank-transfer, was found after the wordlist was utilized.
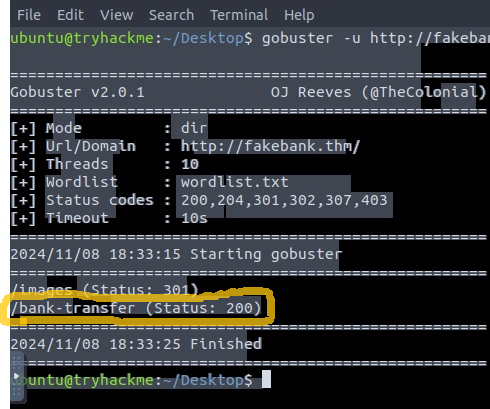
Main Idea & Lesson-Learned In This Lab:
A penetration tester OR security consultant might choose to utilize the Gobuster tool to test a companies web applications for hidden pages that could be potentially exploited.
Working within the command line was fun!

Leave a Reply